Publications for 2007 are listed below. For complete list of earlier publications, use the pointers below.
![]() Complete List of Journal articles
Complete List of Journal articles
![]() List of Other publications
List of Other publications
Popular articles in full text (Norwegian):
![]() Tor Helleseth: Redundans i sikker og pålitlig kommunikasjon
Tor Helleseth: Redundans i sikker og pålitlig kommunikasjon
![]() Tor Helleseth: Sekvenser og anvendelser i mobilkommunikasjon
Tor Helleseth: Sekvenser og anvendelser i mobilkommunikasjon
Short articles:
2007 Publications in International Journals.
P. Charpin, T. Helleseth and V. Zinoviev, Propagation characteristics of 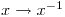 , , Finite Fields and Their Applications 13 (2007), 366-381. |
P. Charpin, T. Helleseth and
V. Zinoviev, The divisibility modulo 24 of
Kloosterman sums on 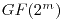 , , 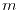 odd,
odd, Journal of Combinatorial Theory, Series A 114 (2007), 332-338. |
| C. Ding, T. Helleseth, T. Kløve and X. Wang, A Generic Construction of Cartesian Authentication Codes, IEEE Transactions on Information Theory 53 (2007), 2229-2235. |
| I. Gancheva and T. Kløve, Generalized Bose-Lin codes, a class of codes detecting asymmetric errors, IEEE Transactions on Information Theory 53 (2007), 1188-1193. |
T. Helleseth, A. Kholosha and G.J. Ness, Characterization of 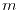 -sequences of length -sequences of length 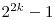 and and 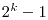 with three-valued crosscorrelation, with three-valued crosscorrelation, IEEE Transactions on Information Theory 53 (2007), 2236-2245. |
T. Helleseth, J. Lahtonen and P. Rosendal, On the Niho type cross-correlation function of 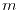 -sequences, -sequences, Finite Fields and Their Applications 13 (2007), 305-317. |
| K.J. Hole, V. Moen, A.N. Klingsheim and K.M. Tande, Lessons from the Norwegian ATM system, Security and Privacy, 5 (2007), 18-24. |
| J. Jedwab and M.G. Parker, There are no Barker arrays having more than two dimensions, Designs, Codes and Cryptography, 43 (2007), 79-84. |
| A. Klingsheim, V. Moen and K.J. Hole, Challenges in securing networked J2ME applications, IEEE Computer, 40 (2007), 24-30. |
| V. Moen, A. Klingsheim, K.I.F. Simonsen and K.J. Hole, Vulnerabilities in e-governments, International Journal of Electronic Security and Digital Forensics, 1 (2007), 89-100. |
| G.J. Ness and T. Helleseth, A new family of ternary almost perfect nonlinear mappings, IEEE Transactions on Information Theory 53 (2007), 2581-2586. |
G.J. Ness and T. Helleseth, A new family of four-valued cross correlation between 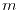 -sequences of different lengths, -sequences of different lengths, IEEE Transactions on Information Theory 53 (2007), 4308-4313. |
| E. Rosnes and Ø. Ytrehus, Turbo decosing on the binary erasure channel: Finite length analysis and turbo stopping sets, IEEE Transactions on Information Theory 53 (2007), 4059-4075. |
| S. Rønjom and T. Helleseth, New attacks on the filter generator, IEEE Transactions on Information Theory, 53 (2007), 1752-1758. |
| R. Yorgova, T. Nishimura and M. Harada, New extremal self-dual codes of length 66, Mathematika Balkanica, 21 (2007), 113-121. |
