2007
P. Charpin, T. Helleseth and V. Zinoviev, Propagation characteristics of 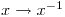 , , Finite Fields and Their Applications 13 (2007), 366-381. |
P. Charpin, T. Helleseth and
V. Zinoviev, The divisibility modulo 24 of Kloosterman sums
on 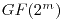 , , 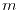 odd,
odd, Journal of Combinatorial Theory, Series A 114 (2007), 332-338. |
| C. Ding, T. Helleseth, T. Kløve and X. Wang, A Generic Construction of Cartesian Authentication Codes, IEEE Transactions on Information Theory 53 (2007), 2229-2235. |
| I. Gancheva and T. Kløve, Generalized Bose-Lin codes, a class of codes detecting asymmetric errors, IEEE Transactions on Information Theory 53 (2007), 1188-1193. |
T. Helleseth, A. Kholosha and G.J. Ness, Characterization of 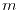 -sequences of length -sequences of length 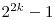 and and 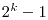 with three-valued crosscorrelation, with three-valued crosscorrelation, IEEE Transactions on Information Theory 53 (2007), 2236-2245. |
T. Helleseth, J. Lahtonen and P. Rosendal, On the Niho type cross-correlation function of 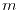 -sequences, -sequences, Finite Fields and Their Applications 13 (2007), 305-317. |
| K.J. Hole, V. Moen, A.N. Klingsheim and K.M. Tande, Lessons from the Norwegian ATM system, Security and Privacy, 5 (2007), 18-24. |
| J. Jedwab and M.G. Parker, There are no Barker arrays having more than two dimensions, Designs, Codes and Cryptography, 43 (2007), 79-84. |
| A. Klingsheim, V. Moen and K.J. Hole, Challenges in securing networked J2ME applications, IEEE Computer, 40 (2007), 24-30. |
| V. Moen, A. Klingsheim, K.I.F. Simonsen and K.J. Hole, Vulnerabilities in e-governments, International Journal of Electronic Security and Digital Forensics, 1 (2007), 89-100. |
| G.J. Ness and T. Helleseth, A new family of ternary almost perfect nonlinear mappings, IEEE Transactions on Information Theory 53 (2007), 2581-2586. |
G.J. Ness and T. Helleseth, A new family of four-valued cross correlation between 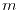 -sequences of different lengths, -sequences of different lengths, IEEE Transactions on Information Theory 53 (2007), 4308-4313. |
| E. Rosnes and Ø. Ytrehus, Turbo decosing on the binary erasure channel: Finite length analysis and turbo stopping sets, IEEE Transactions on Information Theory 53 (2007), 4059-4075. |
| S. Rønjom and T. Helleseth, New attacks on the filter generator, IEEE Transactions on Information Theory, 53 (2007), 1752-1758. |
| R. Yorgova, T. Nishimura and M. Harada, New extremal self-dual codes of length 66, Mathematika Balkanica, 21 (2007), 113-121. |
2006
| Á. Barbero and Ø. Ytrehus, Cycle-logical treatment for "cyclopathic" networks, IEEE Transactions on Information Theory, 52 (2006), 2795-2804. |
| L. Bassalygo, S. Dodunekov, T. Helleseth, and V. Zinoviev, The Grey-Rankin bound for nonlinear codes, Problems of Information Transmission, 42 (2006), 197-203. (Translation of paper in: Problemy Peredachi Informatsi, 42 (2006), 37-44.) |
| P. Charpin, T. Helleseth, and V. Zinoviev, The coset distribution of triple-error-correcting binary primitive BCH codes, IEEE Transactions on Information Theory, 52 (2006), 1727-1732. |
| L. E. Danielsen, T. A. Gulliver, and M. G. Parker, Aperiodic propagation criteria for Boolean functions, Information and Computation, 204 (2006), 741-770. |
| L. E. Danielsen and M. G. Parker, On the classification of all self-dual additive codes over GF(4) of length up to 12, Journal of Combinatorial Theory, Series A, 113 (2006), 1351-1367. |
| H. Dobbertin, P. Felke, T. Helleseth, and P. Rosendahl, Niho type cross-correlation functions via Dickson polynomials and Kloosterman sums, IEEE Transactions on Information Theory, 52 (2006), 613-627. |
| D. V. Duong, G. E. Øien, and K. J. Hole, Adaptive coded modulation with receive antenna diversity and imperfect channel knowledge at receiver and transmitter, IEEE Transactions on Vehicular Technology, 55 (2006), 458-465. |
| T. Helleseth and A. Kholosha, Monomial and quadratic bent functions over the finite fields of odd characteristics, IEEE Transactions on Information Theory, 52 (2006), 2018-2032. |
| K. J. Hole, V. Moen, and T. Tjøstheim, Security in Norwegian Internet banks, IEEE Security and Privacy, 4 (2006), 14-20. |
| T. Kløve, Binary linear codes that are optimal for error correction, Lecture Notes in Computer Science (LNCS), 4123 (2006), 1081-1083. |
G. Leander and A. Kholosha, Bent functions with 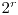 Niho Exponents, Niho Exponents, IEEE Transactions on Information Theory, 52 (2006), 5529-5532. |
| H. Molland and T. Helleseth, Linear properties in T-functions, IEEE Transactions on Information Theory, 52 (2006), 5151-5157. |
G. J. Ness and T. Helleseth, Crosscorrelation of 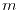 -sequences of different lengths, -sequences of different lengths, IEEE Transactions on Information Theory, 52 (2006), 1637-1648. |
G. J. Ness and T. Helleseth, A new three-valued crosscorrelation distribution between 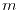 -sequences of different lengths, -sequences of different lengths, IEEE Transactions on Information Theory, 52 (2006), 4695-4701. |
| G. J. Ness, T. Helleseth, and A. Kholosha, On the correlation distribution of the Coulter-Matthews decimation, IEEE Transactions on Information Theory, 52 (2006), 2241-2247. |
| R. Riera and M.G. Parker, Generalized bent criteria for Boolean functions (I), IEEE Transactions on Information Theory, 52 (2006), 4142-4159. |
| R. Riera and M.G. Parker, One and two-variable interlace polynomials: A spectral interpretation, Lecture Notes in Computer Science (LNCS), 3969 (2006), 397-411. |
| E. Rosnes and A. Vahlin, Frequency estimation of a single complex sinusoid using a generalized Kay estimator, IEEE Transactions on Communications, 54 (2006), 407-415. |
| E. Rosnes and Ø. Ytrehus, On the design of bit-interleaved turbo-coded modulation with low error floors, IEEE Transactions on Communications, 54 (2006), 1563-1573. |
| H. G. Schaathun The Boneh-Shaw fingerprinting scheme is better than we thought, IEEE Transactions on Information Forensics and Security, 1 (2006), xx-xx. |
2005
A. Braeken and I. Semaev, The ANF of the composition of addition and multiplication mod 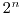 with a Boolean function, with a Boolean function, Proceedings Fast Software Encryption (FSE 2005),Paris, France, Feb. 21-23, 2005, Lecture Notes in Computer Science (LNCS), 3557 (2005), 112-125. |
| W. Chen and T. Kløve, On the second greedy weight for linear codes satisfying the fullrank condition, J. of Systems Science and Complexity 18, no. 1 (2005) 55-66. |
| T. Helleseth, T. Kløve,
and V. Levenshtein, Error-correction capability of binary linear codes, IEEE Trans. Information Theory 51 (2005) 1408-1423. |
| T. Helleseth and P. Rosendahl, New pairs of m-sequences with four-level cross-correlation, Finite Fields and Their Applications 11 (2005) 674-683. |
| T. Helleseth and H.G. Schaathun, The second support weight distribution of the Kasami codes, IEEE Trans. Information Theory 51 (2005) 2892 - 2894. |
| K.J. Hole, E. Dyrnes, and P. Thorsheim, Securing Wi-Fi networks, Computer 38, no. 7 (2005) 28-34. |
| S.-H. Kim, J.-S- No, H. Cheung, T. Helleseth, New cyclic relative difference sets constructed from d-homogeneous functions with difference-balanced property, IEEE Trans. Information Theory 51 (2005) 1155-1163. |
| T. Kløve, P. Oprisan, and B. Bose,
The probability of undetected error for a class of asymmetric error detecting codes, IEEE Trans. Information Theory 51 (2005) 1202-1205. |
| T. Kløve, P. Oprisan, and B. Bose,
Diversity combining for the Z-channel, IEEE Trans. Information Theory 51 (2005) 1174-1178. |
| L. R. Knudsen and J. E. Mathiassen, Preimage and collision attacks on MD2, Proceedings Fast Software Encryption (FSE 2005), Paris, France, Feb. 21-23, 2005, Lecture Notes in Computer Science (LNCS), 3557 (2005), 255-267. |
| L. R. Knudsen, SMASH - A cryptographic hash function, Proceedings Fast Software Encryption (FSE 2005), Paris, France, Feb. 21-23, Lecture Notes in Computer Science (LNCS), 3557 (2005), 228-242. |
| L. R. Knudsen and F. Muller, Some attacks against a double length hash proposal, Proceedings 11th International Conference on the Theory and Application of Cryptology and Information Security (ASIACRYPT 2005), Chennai, India, Dec. 4-8, 2005, Lecture Notes in Computer Science (LNCS), 3788 (2005), 462-473. |
| E. Rosnes and Ø. Ytrehus, Improved algorithms for the determination of turbo-code weight distributions, IEEE Trans. Communication 53 (2005) 20-26. |
| V. Zinoviev, T. Helleseth and P. Charpin, On cosets of weight 4 of binary BCH codes with minimum distance 8 and exponential sums, Problems of Information Transmission 41 (2005) 331-348 [Translated from Problemy Peredachi Informatsii 41 no. 4 (2005) 36-56]. |
2004
| W. Chen and T. Kløve, Finite projective geometries and classification of the weight hierarchies of codes (I), Acta Math. Sinica, Eng. Ser. 20 (2004) 333-348. |
| W. Chen and T. Kløve, On the second greedy weight for linear codes of dimension at least 4, IEEE Trans. Information Theory 50 (2004) 354-356. |
| G. D. Cohen and H. G. Schaathun, Upper bounds on separating codes. IEEE Trans. Inform. Theory 50 (2004) 1291-1295. |
| C.J. Colbourn, T. Kløve,
and A.C.H. Ling, Permutation arrays for powerline communication, IEEE Trans. Inform. Theory 50 (2004) 1289-1291. |
| F-W. Fu and T. Kløve, Two Constructions of Permutation Arrays, IEEE Trans. Inform. Theory 50 (2004) 881-883. |
| T. Helleseth, T. Kløve,
and V. Levenshtein, The simplex codes and other even-weight binary linear codes for error correction, IEEE Trans. Information Theory 50 (2004) 2818-2823. |
| T. Helleseth, J. Lahtonen, and K. Ranto, A simple proof to the minimum distance of -linear Goethals-like codes, J. of Complexity 20 (2004) 279-304. |
| T. Helleseth, J. Lahtonen and P. Rosendahl, On certain equations over finite fields and cross-correlations of m-sequences, Progress in Computer Science and Applied Logic 23 (2004) 169-176. |
| T. Helleseth, M. Maas,
J.E. Mathiassen, and T. Segers Linear Complexity over of Sidel'nikov sequences, IEEE Trans. Information Theory 50 (2004) 2468-2472. |
| T. Helleseth and J. Mykkeltveit, On a proof of Simmons conjecture, Designs, Codes and Cryptography 33 (2004) 39-43. |
| T. Helleseth and H.G. Schaathun,
On the (2,1)-separating weight of the Kerdock code, IEEE Trans. Information Theory 50 (2004) 3312-3315. |
| T. Helleseth and J.F. Voloch, On double circulant quadratic circulant codes, IEEE Trans. Information Theory 50 (2004) 2154-2155. |
| T. Helleseth and V. Zinoviev, On a new identity for Kloosterman sums and nonlinear systems of equations over finite fields of characteristic 2, Discrete Math. 274 (2004) 109-124. |
| T. Helleseth and V. Zinoviev, On weight distributions of shifts of the Goethals-like codes (in Russian), Problems of Information Transmission 40 no. 2 (2004) 19-36. |
| J.W. Jang, Y.S. Kim, J.S. No and, T. Helleseth, New family of p-ary sequences with optimal correlation property and large linear span, IEEE Transactions on Inform. Theory 50 (2004) 1839-1844. |
| Y.S. Kim, J.W. Jang, J.S. No and, T. Helleseth, New constructions of p-ary bent sequences, IEICE Transactions on Fundamentals of Electronics Communications and Computer Sciences} E87-A, no. 2 (2004) 489-494. |
| R.Kristiansen and M.G.Parker, Binary Sequences with Asymptotic Merit Factor > 6.3, IEEE Trans. Information Theory 50 (2004) 3385-3398. |
| V. Moen, H. Raddum, and
K. J. Hole, Weaknesses in the Temporal Key Hash of WPA, Mobile Computing and Communications Review 8, issue 2 (April 2004) 76-83. |
| H. Molland, Improved Linear Consistency Attack on Irregular Clocked Keystream Generators, Proceedings, 2004 Fast Software Encryption, Springer Lecture Notes Computer Science (LNCS) 3017 (2004) 109-126. |
| H. Molland and T. Helleseth, An improved correlation attack against irregularly clocked and filtered keystream generators, in M. Franklin (ed.), Advances in Cryptology-CRYPTO 2004, Springer Lecture Notes Computer Science (LNCS) 3152 (2004) 373-389. |
| J.S. No, D.J. Shin and T. Helleseth, On the -ranks and characteristic polynomials of cyclic difference sets, Designs, Codes and Cryptography 33 (2004) 23-37. |
| H. Raddum, On the computation of coset leaders with high Hamming weight, Discrete Math. 274 (2004) 213-231. |
| E. Rosnes and Ø. Ytrehus, Maximum length convolutional codes under a trellis complexity constraint, J. of Complexity 20 (2004) 372-403. |
| E. Rosnes and Ø. Ytrehus, Sphere-packing bounds for convolutional codes, IEEE Transactions on Inform. Theory 50 (2004) 2801-2809. |
| H. G. Schaathun, A lower bound on the greedy weights of product codes, Designs, Codes and Cryptography 31 (2004) 27-42. |
| H. G. Schaathun, Duality and support weight distributions, IEEE Transactions on Inform. Theory 50 (2004) 862-867. |
| D. Shin, P. V. Kumar and T. Helleseth, An Assmus-Mattson-type approach for identifying 3-designs from linear codes over , Designs, Codes and Cryptography 31 (2004) 75-92. |
| G. E. Øien, H. Holm, and K. J. Hole, Impact of Channel Prediction on Adaptive Coded Modulation Performance in Rayleigh Fading, IEEE Transactions on Vehicular Technology 53 (2004) 758-769. |
2003
| J.-C. Chang, R.-J. Chen, T. Kløve,
and S.-C. Tsai, Distance preserving mappings from binary vectors to permutation, IEEE Trans. Inform. Theory 49 (2003) 1054-1059. |
| W. Chen and T. Kløve, Weight hierarchies of linear codes satisfying the almost chain condition, Science in China, Ser. F - Information Sciences, 46(3) (2003) 175-186. |
| G. Cohen, S. Encheva, S. Litsyn, and H. G. Schaathun, Intersecting codes and separating code, Discrete Applied Mathematics 128 (2003) 75-83. |
| C. Ding, T. Kløve, and M. Golin, Meeting the Welch and Karystinos-Pados Bounds on DS-CDMA Binary Signature Sets, Designs, Codes and Cryptography 30 (2003) 73-84. |
| F.-W. Fu, T. Kløve, Y. Luo, and
V. K. Wei, On equidistant constant weight codes, Discrete Applied Mathematics 128 (2003) 157-164. |
| F. Fu, T. Kløve, and V. Wei, On the Undetected Error Probability for Binary Codes, IEEE Trans. Inform. Theory 49 (2003) 382-390. |
| T. Helleseth, S.H. Kim and J.S. No, Linear complexity over and trace representation of Lempel-Cohn-Eastman sequences, IEEE Transactions on Inform. Theory 49 (2003) 1548-1552. |
| T. Helleseth, T. Kløve, and V.
Levenshtein, Hypercubic 4 and 5-designs from double-error-correcting BCH codes, Designs, Codes and Cryptography 28 (2003) 265-282. |
| L. R. Knudsen and C. J. Mitchell, Analysis of 3gpp-MAC and two-key 3gpp-MAC Discrete Applied Mathematics 128 (2003) 281-292. |
| H. Molland, J.E. Mathiassen, and
T. Helleseth, Improved fast correlation attack using low rate codes, Cryptography and Coding, 9-th IMA International Conference, Cirencester, England, December 16-18, 2003, Springer Lecture Notes Computer Science (LNCS) 2898 (2003) 67-81. |
| E. Rosnes and Ø. Ytrehus, High rate convolutional codes with high cycle weights, Cryptography and Coding, 9-th IMA International Conference, Cirencester, England, December 16-18, 2003, Springer Lecture Notes Computer Science (LNCS) 2898 (2003) 4-23. |
| H. G. Schaathun and W. Willems, A lower bound on the weight hierarchies of product codes, Discrete Applied Mathematics 128 (2003) 251-261. |
| H. G. Schaathun, Fighting two Pirates, Proc. AAECC-15, Toulouse, May 12-16, 2003, Springer Lecture Notes Computer Science (LNCS) 2643 (2003) 71-78. |
| H.G. Schaathun and T. Helleseth, Separating and intersectiong properties of BCH and Kasami codes, Cryptography and Coding, 9-th IMA International Conference, Cirencester, England, December 16-18, 2003, Springer Lecture Notes Computer Science (LNCS) 2898 (2003) 52-65. |
| D. Shin, P. Vijay Kumar and T. Helleseth, 3-Designs from the Goethals codes via a new Kloosterman sum identity, Designs, Codes and Cryptography 28 (2003) 247-263. |
| T. W. Sze, S. Chanson, C. Ding, T. Helleseth
and M.G.Parker, Logarithm Cartesian Authentication Codes, Information and Computation 184 (2003) 93-108. |
| K. Yang and T. Helleseth, On the minimum distance of array codes as LDPC codes, IEEE Transactions on Inform. Theory 49 (2003) 3268-3273. |
2002
| G. Cohen, S. Encheva, and H. G. Schaathun, More on (2,2)-separating systems, IEEE Trans. Inform. Theory 48 (2002) 2606-2609. |
| C. Ding, F. Fu, T. Kløve, and
V. Wei, Constructions of permutation arrays, IEEE Trans. Inform. Theory. 48 (2002) 977-980. |
| C. Ding, T. Helleseth, H. Niederreiter
and C. Xing, The minimum distance of the duals of the binary irreducible codes, IEEE Trans. Inform. Theory. 48 (2002) 2679-2689. |
| N. Hamada and T. Helleseth, The nonexistence of ternary [97,6,63] code Journal of Statistical Planning and Inference 106 (2002) 485-507. |
| T. Helleseth, Sekvenser og anvendelser i mobilkommunikasjon, Nordisk Matematisk Tidsskrift 50 (3-4) (2002) 155-169. |
| T. Helleseth and G. Gong, New nonbinary sequences with ideal two-level autocorrelation function, IEEE Trans. Inform. Theory. 48 (2002) 2868-2872. |
| T. Helleseth and V. Zinoviev, New Kloosterman sums identities over for all , Finite Field and Their Applications 9 (2002) 187-193. |
| L. R. Knudsen, The security of Feistel ciphers with six rounds or less, Journal of Cryptology 15 (2002) 207-222. |
| L. R. Knudsen and E. Biham, Cryptanalysis of the ANSI X9.52 CBCM Mode, Journal of Cryptology 15 (2002) 47-59. |
| L. R. Knudsen and B. Preneel, Construction of secure and fast hash functions using non-binary error correcting codes, IEEE Trans. on Inform. Theory 48 (2002) 2524-2539. |
| L. Knudsen (editor), Advances in Cryptology - EUROCRYPT 2002, Proceedings. Lecture Notes of Computer Science, vol. 2332, Springer Verlag, 2002. |
2001
| K.T. Arasu, C. Ding, T. Helleseth, P.V.
Kumar and H. Martinsen, Almost difference sets and their sequences with optimal autocorrelation, IEEE Transactions on Inform. Theory, 47 (2001), 2934-2943. |
| A. I. Barbero and Ø. Ytrehus, On the bit oriented trellis structure of run length limited codes on discrete local data dependent channels, Discrete Math., 241 (2001), 51-63. |
| M. Bellare, A. Boldyreva, L. Knudsen and C.
Namprempre, On-Line Ciphers and the Hash-CBC Construction, Advances in Cryptology - CRYPTO '2001, Springer Lecture Notes Computer Science (LNCS) 2139 (2001) 292-309. |
| W. Chen and T. Kløve, Relations between the covering and Newton radii of binary codes, Discrete Mathematics 238 (2001), 81-88. |
| W. Chen and T. Kløve, Weight hierarchies of binary linear codes of dimension 4, Discrete Mathematics 238 (2001), 27-34. |
| W. Chen and T. Kløve, On the second greedy weight for linear codes of dimension 3, Discrete Math., 241 (2001) 171-187. |
| W. Chen and T. Kløve, Weight hierarchies of linear codes of dimension 3, Journal of Statistical Planning and Inference 94 (2001), 167-179. |
| C. Ding, T. Helleseth and H. Martinsen, New families of binary sequences with optimal three-level autocorrelation, IEEE Transactions on Inform. Theory 47 (2001), 428-433. |
| C. Ding, T. Kløve and F. Sica, Two classes of ternary codes and their weight distributions, Discrete Applied Mathematics 111 (2001), 37-53. |
| H. Dobbertin, T. Helleseth, V. Kumar
and H. Martinsen, Ternary m-sequences with three-valued crosscorrelation function: Two new decimations, IEEE Transactions on Inform. Theory 47 (2001), 1472-1482. |
| F. Fu, T. Kløve, Y. Luo and
V. Wei, On the Svanström Bound for Ternary Constant Weight Codes, IEEE Transactions on Inform. Theory 47 (2001), 2061-2064. |
| T. Helleseth, P. V. Kumar and H. Martinsen, A new family of ternary sequences with ideal two-level autocorrelation function, Designs, Codes and Cryptography 23 (2001), 157-166. |
| T. Helleseth, C. Rong and K. Yang, New 3-designs for Goethals codes over , Discrete Mathematics 226 (2001), 403-409. |
| T. Helleseth, C. Rong and K. Yang, On t-designs from codes over , Discrete Mathematics 238 (2001), 67-80. |
| T. Helleseth and V. Zinoviev, Codes with the same coset weight distribution as the -linear Goethals codes, IEEE Transactions on Inform. Theory 47 (2001), 1589-1596. |
| T. Helleseth and V. Zinoviev, On coset weight distribution of the -linear Goethals code, IEEE Transactions on Inform. Theory 47 (2001), 1758-1773. |
| K. J. Hole and G. E. Øien, Spectral efficiency of adaptive coded modulation in urban microcellular networks, IEEE Transactions on Vehicular Technology 50 (2001) 205-222. |
| T. Kløve, Relations between the covering and Newton radii of binary codes. Discrete Mathematics 238 (2001) 81-88. |
| T. Kløve and Y. Svirid, Diffuse Difference Triangle Sets, Journal of Statistical Planning and Inference 94 (2001), 255-276. |
| L. R. Knudsen, J. Daemen and V. Rijmen, Linear Frameworks for Block Ciphers, Designs, Codes and Cryptography 22 (2001), 65-87. |
| L. R. Knudsen and T. Jacobsen, Attacks on Block Ciphers of Low Algebraic Degree, Journal of Cryptology 14 (2001), 197-210. |
| L. R. Knudsen and D. Wagner, On the Structure of Skipjack, Discrete Applied Mathematics 111 (2001), 103-116. |
| J.S. No, H. Chung, H.Y. Song, K. Yang, J.D. Lee and
T. Helleseth, New construction for binary sequences of period with optimal autocorrelation using , IEEE Transactions on Inform. Theory 47 (2001), 1638-1644. |
| M.G. Parker, Quantum Factor Graphs, Annals of Telecom., July-August (2001), 472-483. |
| M.G. Parker, Even Length Binary Sequence Families with Low Negaperiodic Autocorrelation, Applied Algebra, Algebraic Algorithms and Error-Correcting Codes, Proceedings of AAECC-14, Melbourne, November 2001. Springer Lecture Notes in Computer Science (LNCS) 2227 (2001) 200-209. |
| M.G. Parker, Spectrally Bounded Sequences, Codes, and States: Graph Constructions and Entanglement, 8th IMA International Conference on Cryptography and Coding, Cirencester, UK, December 2001, Springer Lecture Notes in Computer Science (LNCS) 2260 (2001) 339-354. 200-209. |
| H. G. Schaathun, Upper bounds on weight hierarchies of extremal non-chain codes. Discrete Mathematics 241 (2001) 449-469. |
| H. G. Schaathun, Duality and Greedy Weights of Linear Projective Multisets, Applied Algebra, Algebraic Algorithms and Error-Correcting Codes, Proceedings of AAECC-14, Melbourne, November 2001. Springer Lecture Notes in Computer Science (LNCS) 2227 (2001) 92-101. |
| D. Shin, P. V. Kumar and T. Helleseth, 5-Designs from the lifted Golay code over via an Assmus-Mattson-type approach, Discrete Math., 241 (2001), 479-489. |
2000
| A. Chang, P. Gaal, S.W. Golomb, G. Gong, T. Helleseth
and P. V. Kumar, On a conjectured ideal autocorrelation sequence and a relation to a triple-error-correcting cyclic code, IEEE Transactions on Inform. Theory 46 (2000), 474-485. |
| W. Chen and T. Kløve, Lower bound on K-sequence, Systems Science and Mathematical Sciences 13 (2000), 225-230. |
| C. Ding, T. Helleseth and K. Y. Lam, Duadic Sequences of Prime Lengths, Discrete Math. 218 (2000), 33-49. |
| F. Fu, T. Kløve, and Shu-Tao Xia,
The undetected error probability threshold of m-out-of-n codes, IEEE Trans. Inform. Theory 46 (2000), 1597-1599. |
| N. Hamada and T. Helleseth, Arcs, blocking sets and minihypers, Computers and Mathematic with Applications 39 (2000), 157-169. |
| N. Hamada and T. Helleseth, The nonexistence of some ternary linear codes and update of the bounds for , Math. Japonica 52 (2000), 31-43. |
| N. Hamada, T. Helleseth, H. Martinsen and Ø.
Ytrehus, There is no ternary [28,6,16]-code, IEEE Transactions on Inform. Theory 46 (2000), 1550-1554. |
| K.J. Hole, On classes of convolutional codes that are not asymptotically catastrophic, IEEE Transactions on Inform. Theory 46 (2000), 663-668. |
| K.J. Hole, H. Holm, G. E. Øien
Adaptive Multidimensional Coded Modulation Over Flat Fading Channels, IEEE Journal on Selected Areas in Communications 18 (2000) 1153-1158. |
| K.J. Hole and G. E. Øien Spectral efficiency of adaptive multidimensional coded modulation in urban microcellular networks, IEEE Trans. Veh. Technol. 50 (2000) 205-222. |
| L. R. Knudsen and V. Rijmen, Ciphertext-only Attack on Akelarre. Cryptologia 14, No. 2 (2000). |
| L. R. Knudsen, A Detailed Analysis of SAFER K. Journal of Cryptology 13, No. 4 (2000) 417-436. |
| L.R. Knudsen and W. Meier. Correlations in reduced round variants of RC6. Fast Software Encryption, Seventh International Workshop, New York, USA, April 2000, Springer Lecture Notes in Computer Science (2000) . |
| L. Knudsen, D. Coppersmith and C.J. Mitchell. Key recovery and forgery attacks on the MacDES MAC algorithm. Advances in Cryptology - CRYPTO'2000, Springer Lecture Notes in Computer Science (LNCS) 1880 (2000) 184-196. |
| L. Knudsen and J.E. Mathiassen A chosen plaintext linear attack on DES. Fast Software Encryption, Seventh International Workshop, New York, USA, April 2000. Lecture Notes in Computer Science, Springer Verlag. |
| M.G. Parker, A.H. Kemp and S.J. Shepherd, Fast Blum-Blum-Shub Sequence Generation Using Montgomery Multiplication, IEE Proc-Comput. Digit. Tech. 147 (2000), 252-254. |
| H.G. Schaathun, On weight hierarchy of product codes, IEEE Transactions on Inform. Theory 46 (2000), 2648-2651. |
1999
| W. Chen and T. Kløve Weight hierarchies of extremal non-chain binary codes of dimension 4, IEEE Trans. Inform. Theory 45 (1999) 276-281. |
| Wende Chen and T. Kløve, On the second greedy weight for binary linear codes, Proceedings, AAECC-13, Honolulu, USA, 15-19 Nov. 1999, Springer Lecture Notes in Computer Science vol.\ 1719, 131-141. |
| C. Ding and T. Helleseth, Generalized cyclotomic codes of length , IEEE Trans. Inform. Theory 45 (1999), 467-474. |
| C. Ding, T. Helleseth and K. Y. Lam, Several classes of binary sequences with three-level autocorrelation, IEEE Transactions on Inform. Theory 45 (1999), 2606-2612. |
| I. Duursma, T. Helleseth, C. Rong and
K. Yang, Split weight enumerators for the Preparata codes with applications to designs, Designs, Codes and Cryptography 18 (1999), 103-124. |
| E. Gabidulin and T. Kløve, On the Newton and covering radii of linear codes, IEEE Trans. Inform. Theory 45 (1999), 2534-2536. |
| F.-W. Fu, T. Kløve and S.-Y. Shen, On the Hamming Distance Between Two i.i.d. Random Vectors Over , IEEE Trans. Inform. Theory 45 (1999) 803-807. |
| T. Helleseth, B. Hove and K. Yang, Further results on generalizedHamming weights for Goethals and Preparata codes over , IEEE Transactions on Inform. Theory 45 (1999), 1255-1258. |
| T. Helleseth and H.M. Martinsen, Binary sequences of period with large linear complexity, Information and Computation 151 (1999), 73-91. |
| T. Helleseth, C. Rong and D. Sandberg, New families of almost perfect nonlinear power mappings, IEEE Trans. Inform. Theory 45 (1999), 475-485. |
| T. Helleseth, C. Rong and K. Yang, New Infinite Families of 3-Designs from Preparata Codes over . Discrete Mathematics 195 (1999) 139-156. |
| T. Helleseth and V. Zinoviev, On -linear Goethals codes and Kloosterman sums, Designs, Codes and Cryptography 17 (1999), 268-288. |
| L.R. Knudsen and W. Meier. Cryptanalysis of An Identification Scheme Based on The Permuted Perceptron Problem, Advances in Cryptology - EUROCRYPT'99, Springer Lecture Notes in Computer Science (LNCS) 1592 (1999) 363-374. |
| L. Knudsen, M.J.B. Robshaw and D. Wagner. Truncated Differentials and Skipjack. Advances in Cryptology - CRYPTO'99, Springer Lecture Notes in Computer Science (LNCS) 1666 (1999) 165-180. |
| C. Rong, T. Helleseth and J. Lahtonen, The algebraic decoding of the -linear Calderbank-McGuire code, IEEE Transactions on Inform. Theory 45 (1999), 1423-1434. |
| C. Tellambura, M.G. Parker,Y.J. Guo,
S.J. Shepherd, S.K. Barton, Optimal Sequences for Channel Estimation Using Discrete Fourier Transform Techniques, IEEE Trans on Communications 47 (1999) 230-238. |
| M.G. Parker, Conjectures on the Size of Constellations Constructed from Direct Sums of PSK Kernels, 13th International Symposium, AAECC-13, Honolulu, Hawaii, Lecture Notes of Computer Science Vol. 1719, pp. 420-429, Springer Verlag, 1999. |
1998
| R. Anderson, C. Ding, T. Helleseth and
T. Kløve, How to build robust shared control systems, Designs, Codes and Cryptography 15 (1998) 111-124. |
| K. A. S. Abdel-Ghaffar and Ø. Ytrehus, Difference set codes : codes with squared Euclidean distance of six for partial response channels, IEEE Trans. Inform. Theory 44 (1998) 1593-1602. |
| E. Biham and L. Knudsen, Cryptanalysis of the ANSI X9.52 CBCM Mode, Advances in Cryptology - EUROCRYPT '98, Lecture Notes in Computer Science 1403, 100-111. |
| W. Chen and T. Kløve, Weight hierarchies of linear codes satisfying the chain condition, Designs, Codes and Cryptography 11 (1998) 47-66. |
| W. Chen, Z. Chen and T. Kløve, New constructions of disjoint distinct difference sets, Designs, Codes and Cryptography 15 (1998) 157-165. |
| I. B. Damgård and L. R. Knudsen, Two-key triple encryption, Journal of Cryptology 11 (1998) 209-218. |
| C. Ding and T. Helleseth, On cyclotomic sequencesof order , Information Processing Letters 66 (1998) 21-25. |
| C. Ding and T. Helleseth, New generalized cyclotomy and its applications, Finite Fields and their Applications 4 (1998) 140-166. |
| C. Ding, T. Helleseth and W. Shan, On the linear complexity of Legendre sequences, IEEE Trans. Inform. Theory 44 (1998) 1276-1278. |
| E. R. Hauge and J. Mykkeltveit, The analysis of De Bruijn sequences of non-extremal weight, Discrete Math. 189 (1998) 133-147. |
| T. Helleseth, P. V. Kumar and K. Yang, An infinite family of 3-designs from Preparata codes over , Designs, Codes and Cryptography 15 (1998) 175-182. |
| T. Helleseth, C. Rong
and K. Yang, New infinite families of 3-designs from Preparata codes over , Discrete Math. 195 (1998) 139-156. |
| K. J. Hole, A Comparison of Trellis Modules for Binary Convolutional Codes, IEEE Trans. Commun. 46 (1998) 1245-1250. |
| K. J. Hole, and Ø. Ytrehus, Cosets of convolutional codes with least possible maximum zero- and one-run lengths, IEEE Trans. Inform. Theory 44 (1998) 423-431. |
| L. R. Knudsen, X. Lai and B. Preneel, Attacks on Fast Double Block Length Hash Functions, Journal of Cryptology 11 (1998) 59-72. |
| L. R. Knudsen and B. Preneel, MacDES: a new MAC algorithm based on DES, Electronics Letters 34 (1998) 871-873. |
| K. Yang and T. Helleseth, On the weight hierarchy of Goethals codes over , IEEE Trans. Inform. Theory 44 (1998) 304-307. |
| K. Yang and T. Helleseth, Two new infinite families of 3-designs from Kerdock codes over , Designs, Codes and Cryptography 15 (1998) 201-214. |
1997
| I. Boukliev, S.M. Dodunekov, T. Helleseth
and Ø. Ytrehus, On the (162,8,80;2) codes, IEEE Trans. Inform. Theory 43 (1997) 2055-2056. |
| W. Chen and T. Kløve, Bounds on the weight hierarchies of extremal non-chain codes of dimension 4, Applicable Algebra in Eng., Commun. and Computing 8 (1997) 379-386. |
| W. Chen and T. Kløve, Disjoint sets of distinct sum sets, Discrete Math. 175 (1997) 69-77. |
| W. Chen and T. Kløve, Bounds on the weight hierarchies of linear codes of dimension 4, IEEE Trans. Inform. Theory 43 (1997) 2047-2054. |
| R. Dodunekova, S. Dodunekov, and T. Kløve, Almost MDS and near MDS codes for error detection, IEEE Trans. Inform. Theory} 43 (1997) 285-290. |
| T. Helleseth, T. Kløve
and V. Levenshtein, On the information function of an error correcting code, IEEE Trans. Inform. Theory 43 (1997) 549-557. |
| T. Helleseth, T. Kløve, The Newton radius of codes, IEEE Trans. Inform. Theory 43 (1997) 1820-1831. |
| T. Helleseth and D. Sandberg, Some power mappings with low differential uniformity, Applicable Algebra in Eng., Commun. and Computing 8 (1997) 363-370. |
| K. J. Hole, A note on asymptotically catastrophic convolutional codes of rate (n-1)/n, IEEE Trans. Commun. 45 (1997) 1014-1016. |
| M. F. Hole and K. J. Hole, Low-Complexity Decoding of Partial Unit Memory Codes on Precoded Partial-Response Channels, IEEE Trans. Inform. Theory 43 (1997) 1052-1058. |
| M. F. Hole and K. J. Hole, Tight Bounds on the Minimum Average Weight per Branch for Rate (N-1)/N Convolutional Codes, IEEE Trans. Inform. Theory 43 (1997) 1301-1305. |
| M. F. Hole and Ø. Ytrehus, Two-step trellis decoding of partial unit memory convolitional codes, IEEE Trans. Inform. Theory 43 (1997) 324-330. |
| T. Kløve, On codes satisfying the double chain condition, Discrete Math. 175 (1997) 173-195. |
| V. Kumar and T. Helleseth, An expansion for the coordinates of the trace function over Galois rings, Applicable Algebra in Eng., Commun. and Computing 8 (1997) 353-361. |
| K. Yang and T. Helleseth, On the weight hierarchy of Preparata codes over , IEEE Trans. Inform. Theory 43 (1997) 1820-1831. |
1996
| A.R. Calderbank, G. McGuire, P.V. Kumar and T.
Helleseth, Cyclic codes over , Locator polynomials and Newton's identities, IEEE Trans. Inform. Theory 42 (1996) 217-226. |
| W. Chen and T. Kløve, Lower bounds on multiple distict sums sets, Discrete Math. 148 (1996) 15-35. |
| W. Chen and T. Kløve, On generalization of sonar sequences and inter-modulation-free frequencies assignment sequences, Acta Math. Appl. Sinica 12, no. 1 (1996) 102-108. |
| W. Chen and T. Kløve, The weight hierarchies of -ary codes of dimension 4, IEEE Trans. Inform. Theory 42 (1996) 2265-2272. |
| N. Hamada and T. Helleseth, A characterization of -minihypers and projective ternary [78,5,51;3]-codes, Math. Japonica 43 (1996), 253-266. |
| N. Hamada and T. Helleseth, The uniqueness of [87,5,57:3]-codes and the nonexistence of [258,6,171:3]-codes, Journal of Statistical Planning and Inference 56 (1996) 105-127. |
| N. Hamada and T. Helleseth, A characterization of some -minihypers and some [15,4,9;3]-codes with , Journal of Statistical Planning and Inference 56 (1996) 129-146. |
| E. R. Hauge and J. Mykkeltveit, On the classification of De Bruijn sequences, Discrete Math. 148 (1996) 65-83. |
| E. R. Hauge and T. Helleseth, DeBruijn sequences, irreducible codes and cyclotomy, Discrete Math. 159 (1996) 143-154. |
| T. Helleseth and T. Johansson, Universal Hash functions from exponential sums over finite fields and Galois rings, Advances in Cryptography, Crypto '96, Lecture Notes in Computer Science, 1109, 31-34. |
| T. Helleseth and T. Kløve, The weight hierarchies of some product codes, IEEE Trans. Inform. Theory} 42 (1996) 1029-1034. |
| T. Helleseth and P. V. Kumar, On the weight hierarchies of the semiprimitive codes, Discrete Math. 152 (1996) 185-190. |
| T. Helleseth and P. V. Kumar, New codes with the same weight distributions as the Goethals and the Delsarte-Goethals codes, Designs, Codes and Cryptography 6 (1996) 257-266. |
| T. Helleseth, P. V. Kumar, O. Moreno and
A. G. Shanbag, Improved estimates via exponential sums for the minimum distance -linear trace codes, Â IEEE Trans. Inform. Theory 42 (1996) 1212-1216. |
| T. Helleseth, P. V. Kumar, A. G. Shanbag, Exponential sums over Galois rings and their applications, London Math. Soc. Lecture Notes Series 233 (1996) 109-128. |
| T. Helleseth, P. V. Kumar and A. G. Shanbag, Codes with the same weight distribution as the Goethals codes and the Delsarte-Goethals codes, Designs, Codes and Cryptography 9 (1996) 257-266. |
| T. Kløve, The worst-case probability of undetected error for linear codes on the local binomial channel, IEEE Trans. Inform. Theory 42 (1996) 172-179. |
| T. Kløve, Reed-Muller codes for error detection, the good, the bad, and the ugly, IEEE Trans. Inform. Theory 42 (1996) 1615-1622. |
| T. Kløve, Bounds on the weight distribution of cosets, IEEE Trans. Inform. Theory} 42 (1996) 2257-2260. |
| P.V. Kumar, T. Helleseth, A.R. Calderbank
and R. Hammons, Large families of quaternary sequences with low correlation, IEEE Trans. Inform. Theory 42 (1996), 579-592 |
| C. Rong and T. Helleseth, Use characteristic sets to decode cyclic codes to actual minimum distance, London Math. Soc. Lecture Notes Series 233 (1996) 297-312. |
| A.G. Shanbhaq, P. V. Kumar and T. Helleseth, Upper bound for a hybrid sum over Galois rings with applications to aperiodic correlation of some q-ary sequences, IEEE Trans. Inform. Theory 42 (1996), 250-254. |
| A.G. Shanbhaq, P. V. Kumar and T. Helleseth, Improved binary codes and sequence families from -linear codes, IEEE Trans. Inform. Theory 42 (1996), 1582-1587. |
| K. Yang, T. Helleseth, P. V. Kumar and
A.G. Shanbhaq, On the weight hierarchy of Kerdock codes over , IEEE Trans. Inform. Theory 42 (1996), 1587-1593. |
1995
| N. Hamada and T. Helleseth, A characterization of -minihypers and some -codes (, , ) meeting the Griesmer bound, Discrete Math. 146 (1995) 59-67. |
| N. Hamada and T. Helleseth, A characterization of -minihypers and some [90,5,59;3]-codes meeting the Griesmer bound, Math. Japonica 41 (1995), 657-672. |
| N. Hamada and T. Helleseth, Construction of some optimal ternary linear codes and the uniqueness of the [294,6,195;3]-codes meeting the Griesmer bound, Finite Fields and Applications 1 (1995) 458-468. |
| T. Helleseth, T. Kløve,
V. Levenshtein and Ø. Ytrehus, Bounds on the minimum support weights, IEEE Trans. Inform. Theory 41 (1995) 432-440. |
| T. Helleseth and P. V. Kumar, On the weight hierarchies of the Kasami codes, Discrete Math. 145 (1995) 133-143. |
| T. Helleseth and P. V. Kumar, The algebraic decoding of the -linear Goethals codes, IEEE Trans. Inform. Theory 41 (1995) 2040-2048. |
| K. J. Hole, Cosets of Convolutional Codes
with Short Maximum Zero-Run Lengths, IEEE Trans. Inform. Theory 41 (1995) 1145-1150. |
| T. Kløve, Codes correcting a single insertion/deletion of a zero or a single peak-shift, IEEE Trans. Inform. Theory 41 (1995) 279-283. |
| T. Kløve, Bounds on the worst-case probability of undetected error, IEEE Trans. Inform. Theory 41 (1995) 298-300. |
| P. V. Kumar, T. Helleseth and A.R. Calderbank, An upper bound for Weil exponential sums over Galois rings and applications, IEEE Trans. Inform. Theory 41 (1995) 456-468. |
| Ø. Ytrehus, On the trellis complexity of certain binary linear block codes, IEEE Trans. Inform. Theory 41 (1995) 559-560. |
